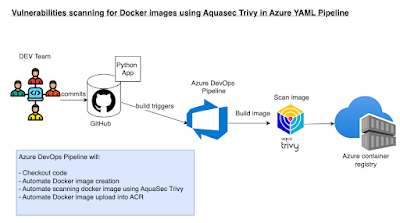
Perform vulnerability scan using Trivy scanner on Azure DevOps Pipeline
Pre-requisites:
- Repo created in ACR, Click here to know how to do that.
- Dockerfile created along with the application source code
- Already created Azure DevOps dashboard in
ADO Yaml Pipeline for scanning docker image using Trivy scanner:
# Docker
# Build and push an image to Azure Container Registry
# https://docs.microsoft.com/azure/devops/pipelines/languages/docker
trigger:
- master
resources:
- repo: self
variables:
# Container registry service connection established during pipeline creation
dockerRegistryServiceConnection: 'd676875f-d1fb-485a-8da4-88d6bfb04604'
imageRepository: 'mypythondockerrepo'
containerRegistry: 'myacrrep31.azurecr.io'
dockerfilePath: '$(Build.SourcesDirectory)/Dockerfile'
tag: '$(Build.BuildId)'
vmImageName: 'ubuntu-latest'
stages:
- stage: Build
displayName: Build and push stage
jobs:
- job: Build
displayName: Build
pool:
vmImage: $(vmImageName)
steps:
# build docker image
- task: Docker@2
displayName: Build Docker image
inputs:
command: build
repository: $(imageRepository)
dockerfile: $(dockerfilePath)
containerRegistry: $(dockerRegistryServiceConnection)
tags: |
$(tag)
# Install Trivy Scanner on Agent
- task: Bash@3
displayName: "Install Trivy"
inputs:
targetType: inline
script: |
curl -sfL https://raw.githubusercontent.com/aquasecurity/trivy/main/contrib/install.sh | sh
# Run Trivy Scan
- task: Bash@3
displayName: "Run Trivy Scan"
inputs:
targetType: inline
script: |
./bin/trivy image --severity HIGH,CRITICAL,MEDIUM --ignore-unfixed $(containerRegistry)/$(imageRepository):$(tag)
# Push docker image
- task: Docker@2
displayName: push Docker image to container registry
inputs:
command: push
repository: $(imageRepository)
dockerfile: $(dockerfilePath)
containerRegistry: $(dockerRegistryServiceConnection)
tags: |
$(tag)
Scan report can be viewed in Build output of Azure Pipelines





No comments:
Post a Comment