Please find steps below for integrating SonarQube to perform static code analysis using Azure DevOps YAML pipeline.
- Azure DevOps Account
- Make sure SonarQube is up and running
- Make sure Java Project is setup, click here for Sample Java Code
- Service connection to connect to GitHub from Azure DevOps using GiHub's PAT(token)
- Service connection to integrate with SonarQube from Azure DevOps
- Make sure you install SonarQube plug-in/Add-on in Azure DevOps using below URL:
How to add SonarQube plug-in in Azure DevOps?
https://marketplace.visualstudio.com/acquisition?itemName=SonarSource.sonarqube
Once added SonarQube plug-in, click on proceed to Organization..
Once added SonarQube plug-in, click on proceed to Organization..
How to integrate SonarQube with Azure DevOps:
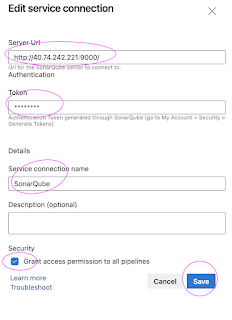
Create Token in SonarQube to authenticate with Azure DevOps
You need to login to SonarQube using your admin password. admin/admin123 and click on Admin on your top side.
Click on My Account, Security.
Under Tokens, Give some value for token name and choose Global analysis token, click on generate Tokens. Copy the token value generated.
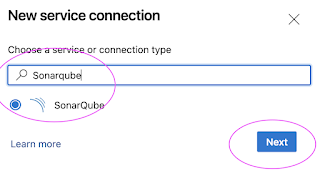
Create Service Connections in Azure DevOps
Login to Azure DevOps. Select your project dashboard.
Click on Project settings --> Service connections
click on New service connection
Give name for service connection and select Grant access permission to all pipelines.
Click on Save.
2. Select your GitHub repo and select the Maven as YAML pipeline template
Create a YAML Pipeline in Azure DevOps
1. Login to Azure DevOps. Go to Azure Pipelines. Click on create a new pipeline, Select GitHub:
3. Click on show assistant on right hand side, type SonarQube and select Prepare Analysis on SonarQube task and then select Service connection from the drop down and choose Integrate with Maven or Gradle option and then click on Add task
Sample Code for entire pipeline is here below
Azure DevOps Pipeline YAML Code:
Azure DevOps Pipeline YAML Code:
# Maven
# Build your Java project and run tests with Apache Maven.
# Add steps that analyze code, save build artifacts, deploy, and more:
trigger:
- master
pool:
vmImage: ubuntu-latest
steps:
- task: SonarQubePrepare@5
inputs:
SonarQube: 'My_SonarQube'
scannerMode: 'Other'
- task: Maven@3
inputs:
mavenPomFile: 'pom.xml'
mavenOptions: '-Xmx3072m'
javaHomeOption: 'JDKVersion'
jdkVersionOption: '1.17'
jdkArchitectureOption: 'x64'
publishJUnitResults: true
testResultsFiles: '**/surefire-reports/TEST-*.xml'
goals: 'clean install sonar:sonar'
- task: PublishTestResults@2
inputs:
testResultsFormat: 'JUnit'
testResultsFiles: '**/surefire-reports/TEST-*.xml'
failTaskOnFailedTests: true
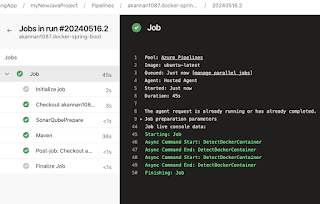
Click on Save and Queue to kick start build.
Now login to SonarQube dashboard, click on Projects
Watch steps in YouTube channel:















No comments:
Post a Comment