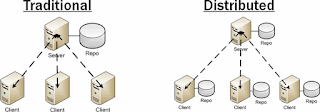
Hashicorp's Terraform is an open-source tool for provisioning and managing cloud infrastructure. Terraform can provision resources on any cloud platform.
Terraform allows you to create infrastructure in configuration files(tf files) that describe the topology of cloud resources. These resources include virtual machines, storage accounts, and networking interfaces. The Terraform CLI provides a simple mechanism to deploy and version the configuration files to Azure.
Watch the steps in YouTube:
- Reduce manual human errors while deploying and managing infrastructure.
- Deploys the same template multiple times to create identical development, test, and production environments.
- Reduces the cost of development and test environments by creating them on-demand.
How to Authenticate with Azure?
Terraform can authenticate with Azure in many ways, in this example we will use Azure CLI to authenticate with Azure and then we will create resources using Terraform.
Pre-requisites:
Azure CLI needs to be installed.
Terraform needs to be installed.
Logging into the Azure CLI
Login to the Azure CLI using:
az login
The above command will open the browser and will ask your Microsoft account details. Once you logged in, you can see the account info by executing below command:
az account list
Now create a directory to store Terraform files.
mkdir tf-acr
cd tf-acr
Let's create a terraform file to use azure provider. To configure Terraform to use the Default Subscription defined in the Azure CLI, use the below cod.
Create Terraform files
Create variable file first
sudo vi variables.tf
location = "southcentralus"
acr_name = "myacrrepo123"
Create main Terraform file
sudo vi main.tf
features {}
}
Perform the below command to initialize the directory.
terraform init
Once directory is initialized, now perform below command to validate terraform files.
terraform validate
Then perform plan command to see how many resources will be created.
terraform plan
terraform apply or terraform apply --auto-approve
Do you want to perform these actions?
type yes
Now Login into Azure Cloud to see the resources created.