Master DevSecOps & Cloud Computing with Coach AK
Engineering DevOps & Cloud Excellence Through Real-World Enterprise Mentorship. 📧 Contact Coach AK: devops.coaching@gmail.com 📱 Call / WhatsApp: +1 (469) 733-5248
Saturday, January 31, 2026
Wednesday, January 28, 2026
How to integrate SonarCloud with Azure DevOps YAML Pipeline | SonarCloud Integration with Azure DevOps | Automate Code Scan using SonarCloud In Azure YAML Pipelines
Please find steps below for integrating SonarCloud to perform static code analysis using Azure DevOps YAML pipeline.

- Azure DevOps Account
- Make sure Java Project is setup in Azure Repos and default branch is either main or master.
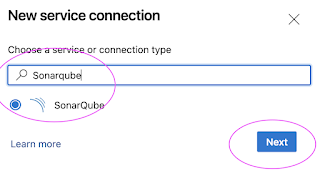
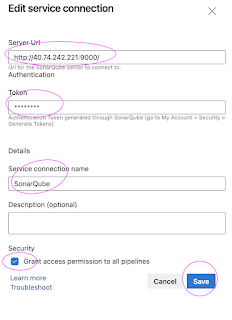
- Service connection to integrate with SonarCloud from Azure DevOps
- Make sure you install SonarCloud plug-in/Add-on in Azure DevOps using below URL:
Azure DevOps Pipeline YAML Code:
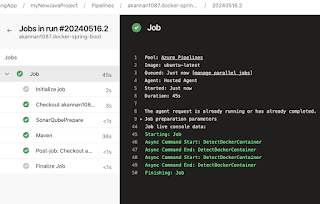
Click on Save and Queue to kick start build.
Now login to SonarCloud dashboard, click on Projects:
How to Integrate SonarCloud with GitHub Actions | GitHub Actions SonarCloud Integration | Automate Static Code Quality Analysis with SonarCloud from GitHub Action
Automate Static Code Quality Analysis in SonarCloud from GitHub Actions:
- Login to https://sonarcloud.io/ and then click on login.

Saturday, January 24, 2026
What is SonarCloud? What is the difference between SonarQube and SonarCloud | SonarCloud vs SonarQube Server Explained

SonarCloud is a
cloud-based code quality and security analysis tool.
-
It automatically scans your code to find:
- Bugs
- Security vulnerabilities
- Code smells (bad coding practices)
- Managed by SonarSource
- Works directly with cloud CI/CD pipelines
- No server installation or maintenance needed
👉 Think of SonarCloud as a “code quality checker in the cloud”
🧠 Why SonarCloud Matters in DevOps
- Detects issues early in CI/CD pipelines
- Prevents bad or insecure code from reaching production
- Enforces Quality Gates (pass/fail rules)
- Improves Code maintainability, Security posture, Team collaboration
☁️ What Is SonarQube?
- SonarQube is the self-hosted version of Sonar’s code analysis platform
- You install and manage it On-prem servers or Virtual machines or Kubernetes
- Requires Server setup, Database & maintenance
👉 Think of SonarQube as “code quality on your own servers”
🔄 SonarQube vs SonarCloud (Easy Comparison)
| Feature | SonarQube | SonarCloud |
|---|---|---|
| Hosting | Self-hosted (on-prem or private cloud) | Fully cloud-hosted (SaaS) |
| Setup | Manual install & config | No setup needed |
| Maintenance | You manage servers, upgrades, scaling | Zero maintenance, Sonar handles everything |
| Cost | Free + paid tiers for advanced features | Subscription based on lines of code; free for public repos |
| Data Control | Full control over data and environment | Data stored in SonarCloud’s infrastructure |
| Best For | Enterprises, regulated orgs | Cloud & DevOps teams |
| Integrations | Works with most CI/CD systems, including on-prem | Deep integration with GitHub, GitLab, Bitbucket Cloud, Azure DevOps |
| Branch/PR Analysis | Requires Developer Edition or higher | Included by default |
| Customization | Supports plugins, custom rules, and deep configuration | More limited customization compared to SonarQube |
| Scalability | You scale it | Auto-scales |
When Should You Use SonarCloud?
- You use GitHub / Azure DevOps / Bitbucket
- You want quick setup
- You don’t want to manage servers
- You’re building Cloud-native apps or DevSecOps pipelines or Open-source projects
🧠 Additional Context (Industry Understanding)
Even though the article highlights practical differences, other sources also emphasize technical nuance:- Both tools use the same core analysis engine (so results and rules are similar), but SonarCloud is optimized for cloud workflows and integrates first-class with GitHub, GitLab, Bitbucket, and Azure DevOps.
- SonarCloud is typically easier to start with because it’s SaaS, but enterprises with strict compliance might prefer SonarQube’s on-prem deployment options.
📝 Final Thoughts
- SonarCloud = Best for modern DevOps & cloud teams
- SonarQube = Best for enterprise & on-prem needs
- Both help you shift-left security and quality
👉 If you’re learning DevOps, DevSecOps, or CI/CD, mastering SonarCloud is a must.
SonarCloud is ideal for teams who want zero maintenance and fast cloud adoption. SonarQube is best for organizations needing data control, customization, and on‑prem compliance.How to Integrate SonarCloud with Jenkins | Jenkins SonarCloud Integration | Automate Static Code Quality Analysis with SonarCloud from Jenkins
Automate Static Code Quality Analysis with SonarCloud from Jenkins
Pre-requisites in SonarCloud:
- Login to https://sonarcloud.io/, click on login.

Pre-requisites in Jenkins:
def mvnHome = tool 'Maven3'
stage ("checkout") {
stage ('build') {
sh "${mvnHome}/bin/mvn clean install -f MyWebApp/pom.xml"
}
stage ('Code Quality scan') {
withSonarQubeEnv('SonarCloud') {
}
Friday, January 2, 2026
Master DevSecOps and Multi Cloud Computing Course by Coach AK | DevSecOps and Cloud Computing Online Classes | Jan/Feb 2026 Schedule
Live Hands-On Bootcamp – Jan/Feb 2026
 🚀 Supercharge your DevOps career with real-world skills!
🚀 Supercharge your DevOps career with real-world skills!
🔥 What You’ll Learn
👉 Master leading DevSecOps tools & cloud platforms including:
✔ Git, GitHub, Bitbucket, Azure Repos
✔ Jenkins, GitHub Actions, Azure DevOps
✔ SonarQube, Trivy, Nexus, Slack
✔ Terraform, Ansible
✔ Docker & Kubernetes
✔ Helm, Prometheus & more!
🌐 AWS & Azure Multi-Cloud Training Included!
🧠 Real-World, Practical Training
✔ 100% Hands-On Projects
✔ Live Interactive Sessions
✔ Career Support: Resume + Interview Prep
✔ Build Recruiter-Ready Skills!
📅 Schedule Options
📍 Weekend Batch
🗓 Starts Jan 31, 2026
🕤 Sat – 09:45 AM to 11:30 AM CST
🕥 Sun – 10:30 AM to 12:30 PM CST
📍 Weekday Evening Batch
🗓 Starts Feb 12, 2026
🕕 Tue & Thu – 6:00 PM to 8:00 PM CST
🌎 Online – Learn From Anywhere!
📌 Why Join This Bootcamp?
✅ Industry-Relevant Projects
✅ Expert Coaching by Coach AK
✅ Flexible Schedules for Working Pros
✅ Multi-Cloud + Security Focus
✅ Networking & Career Growth Support
📞 Register Now – Spots Are Limited!
📱 +1 (469) 733-5248 (WhatsApp Available)
📧 devops.coaching@gmail.com
➡ Early Bird Discounts Available!
🚀 Take the Next Step in Your DevOps Career!
💡 Learn with confidence. Build with purpose. Get hired faster.
-
Let us learn how to create and configure a Self-Hosted Agent in Azure DevOps (ADO). What is an Agent? An agent is computing infrastructure w...
-
Please find steps for integrating SonarQube with GitHub Actions: Pre-requisites: Make sure SonarQube is up and running Make sure Java Projec...
-
What is Amazon EKS Amazon EKS is a fully managed container orchestration service. EKS allows you to quickly deploy a production ready Kubern...